Cyber Security: The final frontier…
This is a “starting point” for anyone starting out in Cyber Security; specifically someone looking to get into Security Engineer, Network Security Administrator, or Security Analyst.
See also: get into cybersecurity 2026.
If you’re interested in hands-on security testing, check out our comprehensive penetration testing guide for beginners which covers ethical hacking methodologies and essential tools.
The OSI/TCP Model
The OSI Model gives you an idea of how information is transmitted and the process in which it occurs down to the most physical level. Most organizations, however, prefer the TCP Model. Understanding how information is transmitted is crucial for anyone looking to get into security, which is why this is literally the first thing that I have put down.
- The OSI Model: https://www.cloudflare.com/learning/ddos/glossary/open-systems-interconnection-model-osi/
- The TCP Model: https://www.guru99.com/tcp-ip-model.html
Additionally, understanding wireshark (or other packet capture tools), nmap, and network protocols in general is a really good starting point.
Information Security
Information Security, well, starts with the CIA Triad:
- Confidentiality: https://whatis.techtarget.com/definition/confidentiality
- Integrity: https://whatis.techtarget.com/definition/integrity
- Availability: https://whatis.techtarget.com/definition/availability
Information Security Frameworks
You should probably study or at least understand the concepts behind NIST and other InfoSec Frameworks. These frameworks not only provide a standard for organizations to adhere to, but they also provide a foundation for policies, procedures, and other important concepts within Cyber Security.
You might also find our breaking into software development with no experience helpful.
- NIST: https://www.nist.gov/cyberframework
- CIS: https://www.cisecurity.org/controls/
- CMMC: https://www.acq.osd.mil/cmmc/
Auditing, Compliance, and Governance

Policies and Procedures are the administrative portion of Cyber Security. Policies govern the overall security of an organization while procedures detail the steps of meeting those policies.
- Information Security Policy Design: https://resources.infosecinstitute.com/category/enterprise/governance/information-security-policy/information-security-policy-design-tips-keep-mind/
- Definition of Security Policy: https://searchsecurity.techtarget.com/definition/security-policy
- SANS Policies and Templates: https://www.sans.org/security-resources/policies/
Good rule of thumb: Policies + Procedures = Compliance.
Understanding the Threat Landscape

- Cyber Threat Landscape: https://rapidscale.net/resources/blog/blog-post/cyber-threat-landscape
- What are the Most Common Attacks: https://www.cisco.com/c/en/us/products/security/common-cyberattacks.html#~types-of-cyber-attacks
- MITRE ATT&CK: https://attack.mitre.org/
- Cyber Kill Chain: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
- OWASP Top Ten: https://owasp.org/www-project-top-ten/
In order to know what you’re protecting against… Well, it helps to know what you’re protecting against. (Lol.) If you don’t- it’s going to be quite difficult to pinpoint. There are many different types of attacks from various vectors and it’s imperative that you know how to detect and define these attacks.
Related: Learn about build a home lab that actually gets you hired.
Not only that, look up what phishing is, common malware and ransomware attacks, keep yourself up to date with breaches, and study on “social engineering” as a concept.
Security Tools and Solution Sets
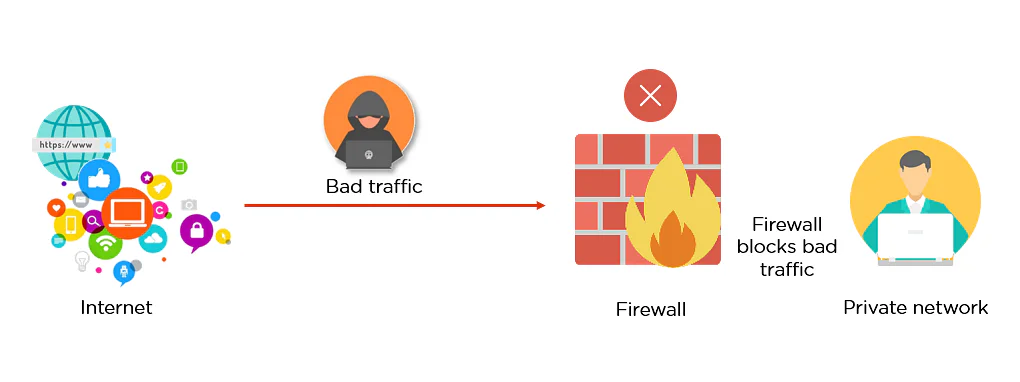
- Security Gateways (Aka “Firewalls”)
- Endpoint Protection (Aka “Anti-Virus”)
- Email Filtering
- Data Encryption
- Mobile Device Management
- Mobile Device Security
- Site to Site VPN
- Remote User Access VPN
- Security Scanning Tools
- Cloud IaaS, SaaS, and PaaS Protections
- IoT Security
- SCADA and ICS Security
- Workload Security (Serverless, Container Security)
- Phish Test Simulations
- User Education Programs
The list could go on and on, but you get the idea. Security is not only a set of solutions, but it is also a mindset. Ideally, you should have solutions or products to fill these gaps, but ultimately, an organization is only as strong as their “weakest user.” A healthy combination of these solution sets and an educational approach is needed.
These items, for some organizations, can also lend to your area of interest within security. Some businesses with larger security teams segment these responsibilities while others expect their team members to “wear many hats” and understand ALL of these. There is a high demand for security professionals, but an even higher demand for such professionals that know Cloud, IoT, and other more specific fields.
For more insights, check out our guide on cissp requirements 2026: $129k+ security career path.
Knowing Normal and Finding Evil

- Anomaly Detection: https://www.informationsecuritybuzz.com/articles/finding-unknown-threats-anomaly-detection/
- SANS Poster: https://digital-forensics.sans.org/media/SANS_Poster_2018_Hunt_Evil_FINAL.pdf
Now, that you know the basics, you can focus on finding threats. Knowing Normal and Finding Evil requires a basic knowledge of infrastructure and what native programs should be running, although, it’s more dependent on troubleshooting tactics and critical analysis than it is anything else. Another segment of this delves into forensics, though, I won’t harp on that too much as it can be considered more advanced.
More on Forensics: https://niccs.us-cert.gov/workforce-development/cyber-security-workforce-framework/digital-forensics
Incident Response and SOC
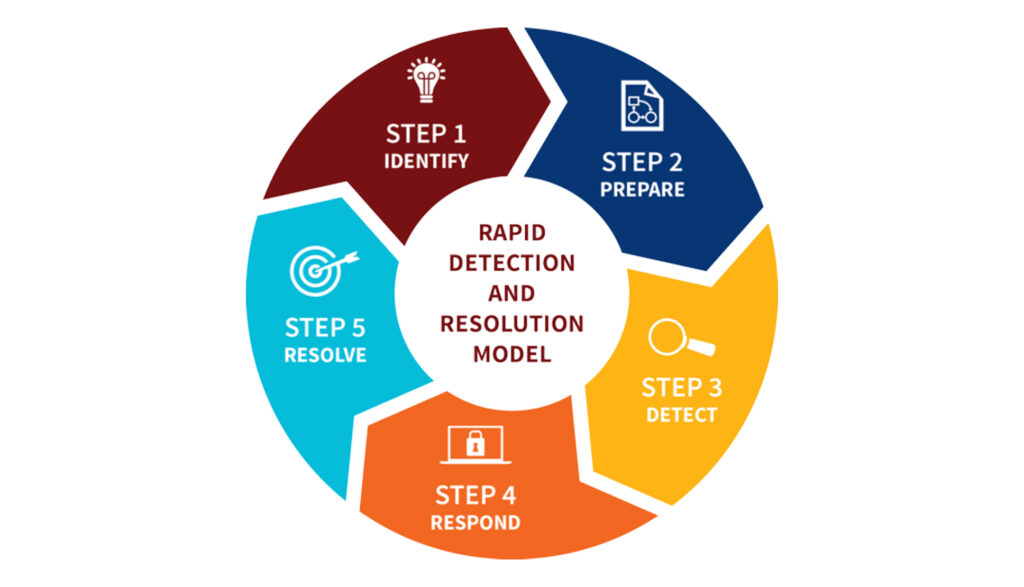
- Incident Response Basics: https://searchsecurity.techtarget.com/definition/incident-response
- Incident Response Planning: https://www.securitymetrics.com/blog/6-phases-incident-response-plan
- What is a SOC: https://en.wikipedia.org/wiki/Security_operations_center
- SOC definition: https://en.wikipedia.org/wiki/Information_security_operations_center
Incident Response is the process of preparing for, detecting, mitigating, and responding to an incident. An incident is defined as a breach or attack of an organization’s security that affects its integrity or availability and/or the unauthorized or attempted access to a system or systems.
It’s important that the above information is understood because a large portion of Incident Response revolves around preventative measures, as well as what to do after (or if) an incident occurs. Additionally, the follow-up and post mortem components are key to building for a better tomorrow. A Security Operations Center, or SOC, is a centralized unit that deals with security issues on an organizational and technical level. Not all organizations have a SOC, though some verticals require it.
Also, if you can get comfortable with Linux and Python, that’s a plus.
(It doesn’t have to be Kali, per se.)
- Getting Started with Kali Linux: https://kali.training/lessons/2-getting-started-with-kali/
- Kali Linux Install: https://www.kali.org/docs/installation/
- Getting Started with Python: https://www.python.org/about/gettingstarted/
There is a lot to know and learn, but these are all great places to start.
Tips for applying:
- Always research the company you’re applying for. (Know their history, CEO, mission statement, breach history, etc.)
- Be up front about what you know or don’t know. (Don’t embellish too heavily.)
- Ask about any mentorship or junior-level programs they may have available.
- Be yourself! (Duh!)
- Familiarize with common security vendors or even try to get insight to what the company uses prior to the interview. (Don’t weaponize any breach info, only use it tactfully or “as a matter of factly”- if applicable.)
- Acknowledge that you’re willing to learn and that “there’s always more that you don’t know.”
- Set up a testing lab at home, if possible, and use your initiative to your advantage. (Show them any projects or findings you’ve been working on, if necessary.)
Other suggestions:
- Find a mentor that’s willing to teach you
- Join Twitter and connect with Cyber Security Professionals
- Stay active on LinkedIn
- Pursue security certifications, if applicable
- Go to local (or remote) security conferences
- Subscribe to RSS Feeds and security news sites
- Contribute to the community by testing things and sharing results
- Learn and speak on topics
Good luck!